Over the past several years, and even more so this year, we’ve seen an explosion of cyberthreats. For individuals, this typically involves a loss of personal data and the uncertain feeling that our private information is available freely on the internet. For businesses and corporations, though, the price is even higher. Ransomware attacks and the fallout from security breaches can easily cost a company upwards of $3.9 million in legal fees, ransoms, and customer turnover.
Today’s executive leaders and management teams are facing unprecedented challenges as they develop strategies to run efficient, profitable and secure businesses. When cyberthreats are all around, it can be very intimidating to think about managing cybersecurity on your own. The National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) continues to play an important role in the vital business functions of risk assessment, compliance, investment to increase capabilities and results evaluation.
This Cybersecurity Awareness Month, we wanted to highlight and summarize the key benefits to building a NIST-aligned cybersecurity program for your organization.
How the NIST Cybersecurity Framework Can Benefit Your Business
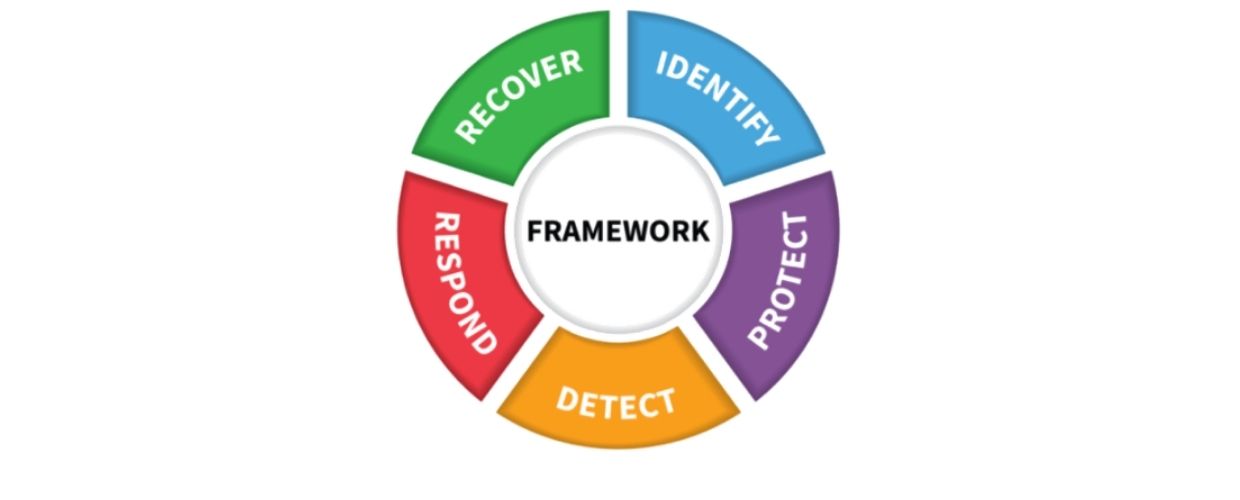
In 2014, NIST released its Cybersecurity Framework, which was intended to integrate industry standards and best cybersecurity practices into a simple series of 5 easy-to-understand functions: Identify, Protect, Detect, Respond and Recover. How can these functions help your business succeed?
1. Get your leadership team on the same cyber page
Before you can take action, you must identify areas of concern within your current network and take steps to mitigate gaps in your computer security. The framework offers this much-needed context, allowing business leaders and managers across business units to be better equipped to understand cybersecurity preparedness and resiliency, the benefits of controls compliance, and the value proposition around cybersecurity investments.
Action item: Write up an agreement so everyone is on the same page. Try a pilot program, so you can learn what works and what doesn’t before implementing it across your entire organization.
2. Tailor the framework to your business
A key element of great network security is establishing a barrier around your systems and sensitive data. 80% of firms have seen an increase in cyberattacks in 2020. With the framework, hundreds of detailed security controls are progressively rolled up into 98 subcategories, 22 categories and 5 life cycle functions. The result is a flexible instrument that can be tailored to your business. From the server room to the executive conference room, the framework offers easy-to-understand language, allowing cyber risks to be expressed to operations, human resources, accounting professionals and more.
Action item: Partner with a trusted Managed Security Services Provider (MSSP) like Deerwood Technologies to customize your cybersecurity plan to meet your unique business needs. Nothing is set in stone. Be able to communicate a clear understanding of your operational, organizational and individual cyber risk. On average, it takes 206 days for an organization to detect a breach, which is too late to stop it. That’s why this step is so important.
3. Finding your cyber “gaps” and fixing them
Creating content around cybersecurity information represents an ongoing communication challenge, as it can often be too technical, and not especially helpful, to business leaders. The framework profile can provide guidance to clearly define a proactive game plan. It allows you to organize cybersecurity compliance and investment data for cybersecurity analysis, discussion and decision-making. It provides the context needed to allow everyone in an organization to participate in the cybersecurity risk management discussion in a meaningful way.
Action item: Compare your “current” profile that defines current risk management practices to a “preferred” profile that outlines the outcomes needed to achieve the desired cybersecurity risk management goals. This important exercise results in a gap analysis that can be used to deploy actions required to meet overall business goals and to prioritize activities for cost-effective allocation of capital and talent resources.
Then, identify the actions that need to be taken to get you there and prioritize them based on importance, project requirements, budget and staff availability.
An effective incident response plan can shorten your recovery time
When a threat or a breach in your system is detected, your IT team must take quick and decisive action. Currently, the average time from breach to containment is 314 days.
4. Active implementation
Now that you have established a meaningful cybersecurity dialogue between IT staff, managers, officers and boards, you can quickly begin to work towards more effective risk assessment, prudent investments, monitoring and adjustment of risk reduction.
Action item: Stop crossing cybersecurity activities off your list. This is not the end. Cybersecurity is a continual, ongoing process. You’ll need to revisit these steps regularly throughout the year.
After a cyberattack, focus on recovery and getting back to normal.
Do you know what your company should do to get back on track after a breach?
Having a recovery plan is only one key step in establishing a proactive cybersecurity program. Once you’ve responded to the threat, ensure your plan addresses how to prevent similar future incidents and maintain your compliance.
Establish a Proactive Cybersecurity Plan for Your Business
A solid cybersecurity plan based on the NIST framework provides a unique business capability. Deerwood Technologies guides businesses to develop their cybersecurity program, aligned with the functions of cybersecurity recommended by the NIST. With our team of experts on your side, you can focus on what truly matters: growing your business and supporting your staff and customers.
Contact us today to learn more about your risks and how we can help enhance the cybersecurity profile of your business.