October is Cybersecurity Awareness Month. Now, in its 18th year, Cybersecurity Awareness Month exists to help Americans develop an appreciation and awareness of the importance of cybersecurity. One of the focus areas of this year’s campaign is phishing. And with good reason. Consider the following statistics:
- The Federal Bureau of Investigation (FBI) reported over 240,000 instances of phishing in 2020 – a 110% increase from 2019
- There were 11 times as many phishing complaints in 2020 as compared with 2016
- Globally, 75% of organizations experienced a phishing attack last year
- 96% of phishing attacks were perpetrated via email
While cybercrime has been rising steadily for years, COVID-19 provided a host of opportunities for cybercriminals who were quick to exploit the global pandemic for their nefarious means, most notably through COVID-related fraud around the Coronavirus Aid, Relief, and Economic Security (CARES) Act.
What is phishing?
Computerworld describes the origins of phishing as follows:
“The word phishing was coined in 1996 by hackers stealing America Online accounts and passwords. By analogy with the sport of angling, these internet scammers were using email lures, setting out hooks to ‘fish’ for passwords and financial data from the ‘sea’ of internet users. They knew that, although most users wouldn’t take the bait, a few likely would.”
With a phishing attack, the perpetrator sends unlawful emails, asking for personal information or credentials (perhaps a pin number). Oftentimes, these emails are disguised and appear to be sent from a company or service that the recipient uses and may redirect the individual to a phony website in the hope that users will bite and provide the information they ask for, such as credit card numbers, account numbers, passwords, usernames, and other valuable information. This information can be used to access important accounts, resulting in identity theft and financial loss.
Phishing is a form of social engineering, which is the art of manipulating people in order to gain access to buildings, systems, or data through the cloud. While email is the most common medium for phishing attacks, text messages, direct messaging, social media, and video games are also used in order to get people to respond with their personal information. Phishing attacks have one characteristic in common: They are designed to trigger emotions such as curiosity, compassion, fear, and greed.
How can you spot a phishing attack?
Phishing emails are one of the most common online threats, and it is important to know the telltale signs and know what to do if you see them. Here are a few rules of thumb in helping to identify phishing attacks:
- A legit organization will never send you an email asking for passwords, credit card information, credit numbers, or tax numbers, and also will not send the link you need to log in – if the company you are dealing with needs information about your account, the email should refer to you by name and instruct you to contact them by phone
- Check email addresses carefully – cybercriminals often use an email address that resembles one of a reputable company, but has been modified to omit a few characters
- A general greeting such as “Dear Customer” or “Sir” and missing contact information or a signature block are strong indicators of a phishing email
- Be alert when you receive a suspicious, urgent, or threatening email from a company
The Cybersecurity & Infrastructure Security Agency (CISA) has provided a number of resources in support of Cybersecurity Awareness month, and has also shared these general cybersecurity tips:
- Use multifactor authentication on all accounts and devices
- Be password-savvy, get creative and avoid using use the same password for multiple accounts
- Protect all devices with anti-virus software
- Limit the information you post on social media
- Before connecting to public wireless hotspots, confirm with staff that the network is legitimate
Examples of phishing attacks
While there are some definite telltale signs of phishing attacks, as identified above, they can also be incredibly well done. Cybercriminals have come a long way from the Nigerian prince days of yore. And since seeing is believing, we have included a few examples below.
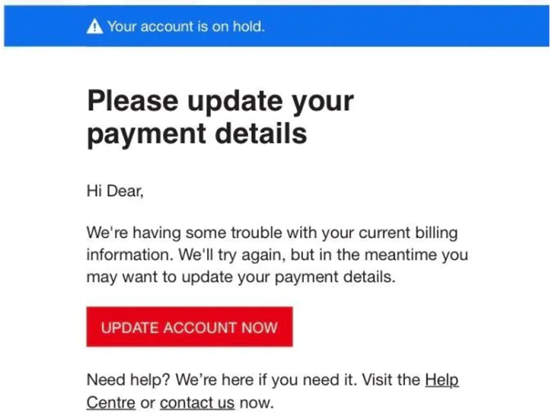
This email, purporting to be from Netflix, is one that has been making the rounds. Recipients are encouraged to update their account by providing their credit card information.
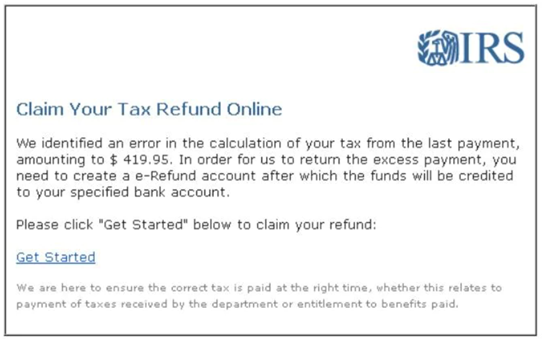
The Internal Revenue Service (IRS) will never send an email asking for your banking information, like in this fraudulent email example.
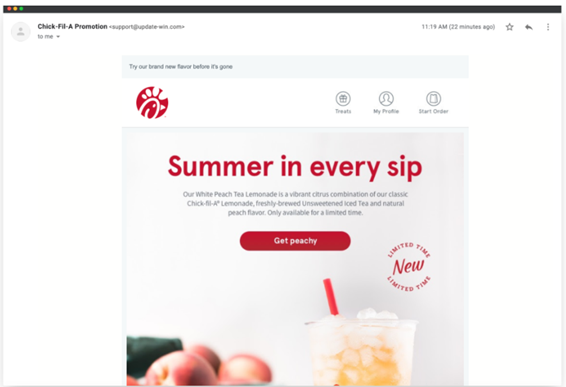
Even Chick-fil-A isn’t safe from cybercriminals.
Keeping Yourself and Your Organization Cybersafe
The theme for Cybersecurity Awareness month is Do Your Part. #BeCybersmart. Sound advice. And one of the best ways to be cybersmart is by working with the right Managed Services Provider (MSP) partner, one that is up to speed on the latest and greatest in the constantly evolving field of cybersecurity and cloud computing, and one that is committed to keeping you and your organization secure. Deerwood Technologies is that right MSP partner. By taking the time to get to know your business and your organizational requirements, Deerwood Technologies is able to customize IT solutions that are in line with your strategic goals and constraints, and all within your budget. Reach out today and #BeCybersmart.

