Cybersecurity is a critical concern for businesses of all sizes, as protecting sensitive information and maintaining IT system integrity are paramount. The National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework to help organizations build robust cybersecurity strategies through a structured approach to managing and mitigating risks. Now, after a decade, the NIST Cybersecurity Framework has received its first significant update with the release of version 2.0, introducing several enhancements to address evolving cybersecurity threats and challenges.
What Is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a comprehensive set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. It was developed through collaboration between industry experts, government agencies, and academic institutions to provide a standardized approach to cybersecurity.
Key Components of the Framework
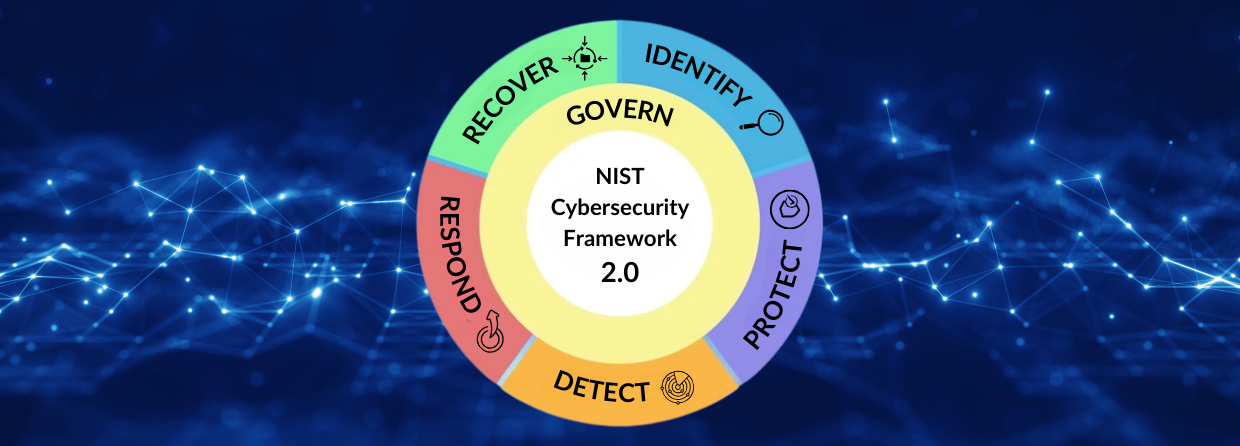
The framework is organized into six core functions, each representing a key aspect of cybersecurity management:
Govern
- Establishes clear cybersecurity policies and responsibilities within the organization.
- Ensures cybersecurity efforts align with overall business objectives and risk management strategies.
Identify
- Involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities.
- Key activities include asset management, business environment understanding, governance, risk assessment, and risk management strategy.
Protect
- Focuses on implementing safeguards to ensure the delivery of critical services and to protect systems and data.
- Includes activities such as access control, awareness and training, data security, information protection processes and procedures, maintenance, and protective technology.
Detect
- Entails developing and implementing activities to identify the occurrence of cybersecurity events promptly.
- Key activities include anomalies and events detection, continuous monitoring, and detection processes.
Respond
- Involves taking action regarding a detected cybersecurity event to mitigate its impact.
- Includes response planning, communications, analysis, mitigation, and improvements.
Recover
- Focuses on maintaining plans for resilience and restoring any capabilities or services impaired due to a cybersecurity incident.
- Key activities include recovery planning, improvements, and communications.
Benefits of Adopting the Framework
Organizations that adopt the NIST Cybersecurity Framework can benefit in several ways:
1. Enhanced Risk Management
Provides a structured approach to identifying and managing cybersecurity risks, helping organizations prioritize their efforts and allocate resources effectively.
2. Improved Security Posture
Implementation of best practices and guidelines improves overall cybersecurity defenses, reducing the likelihood of successful attacks.
3. Compliance
Aligns with various regulatory and industry requirements, helping organizations meet compliance obligations.
4. Flexibility
The framework is adaptable to different types of organizations and can be tailored to specific needs and contexts.
5. Stakeholder Confidence
Demonstrates a commitment to cybersecurity, building trust with customers, partners, and other stakeholders.
By leveraging the NIST Cybersecurity Framework, organizations can develop a robust cybersecurity strategy that addresses current and emerging threats, ensuring the protection of critical assets and data.
NIST Cybersecurity Framework 2.0
The NIST Cybersecurity Framework has been pivotal in managing cybersecurity risks. After ten years of technological advancements and evolving threats, NIST has released the first major update: NIST Cybersecurity Framework 2.0. This update addresses new challenges, incorporates a decade of feedback, and reflects the latest best practices to guide organizations through modern cybersecurity complexities.
Differences Between the Original Framework and 2.0
The original framework provided a solid foundation for cybersecurity practices. The 2.0 version builds on this by expanding its focus areas to include more detailed guidance on managing a broader spectrum of cybersecurity risks. This includes a stronger emphasis on privacy and the intersection between cybersecurity and other business functions.
Introduction of the “Govern” Function
A major new feature in the NIST Cybersecurity Framework 2.0 is the “Govern” function. This part focuses on creating and maintaining clear rules and responsibilities for cybersecurity within an organization. It involves setting up policies and defining who is responsible for what, making sure these rules fit well with the organization’s overall strategy for managing risks. By adding this function, NIST underscores the importance of strong leadership and supervision in cybersecurity, ensuring that cybersecurity is not treated as a separate issue but is integrated into the organization’s main goals and decisions.
New Emphasis on Supply Chain Risk Management
One of the most significant additions to the NIST Cybersecurity Framework 2.0 is the focus on supply chain risk management. The update recognizes that an organization’s cybersecurity is only as strong as its weakest link, which often lies in its supply chain. The new guidelines help businesses identify, assess, and mitigate risks associated with third-party vendors and suppliers.
Enhanced Guidelines for Small and Medium-Sized Businesses
Acknowledging the unique challenges faced by SMBs, the 2.0 framework includes enhanced guidelines specifically designed for smaller organizations. These guidelines are tailored to be more manageable and practical for businesses with limited resources, helping them implement effective cybersecurity measures without being overwhelmed.
Integration of Emerging Technologies and Threats
The updated framework incorporates considerations for emerging technologies such as AI, IoT, and cloud services. This integration helps organizations address the new risks introduced by these technologies, ensuring that cybersecurity measures keep pace with technological advancements.
Improvements in Usability and Clarity
One of the key improvements in the 2.0 framework is its enhanced usability and clarity. The language has been refined to be more straightforward, and the structure has been reorganized to make it easier for organizations to navigate and implement. This makes the framework more accessible to a wider range of users, from cybersecurity professionals to business executives.
Updates to Core Functions and Implementation Tiers
The core functions (Identify, Protect, Detect, Respond, Recover) remain central to the framework, but they have been updated to reflect current best practices and standards. Additionally, the implementation tiers, which guide organizations in assessing their cybersecurity maturity, have been refined to provide clearer guidance and better alignment with real-world practices.
These updates in the NIST Cybersecurity Framework 2.0 provide organizations with a more comprehensive and practical approach to managing cybersecurity risks in today’s complex digital environment. By adopting these enhanced guidelines, businesses can strengthen their cybersecurity posture and better protect their critical assets and data.
Actionable Steps for Business Owners
Enhance your cybersecurity posture by leveraging the updated NIST Cybersecurity Framework 2.0 with these key steps:
Review and Understand the New Framework Guidelines
- Thoroughly review the updated guidelines to understand new requirements and best practices.
- Conduct a gap analysis to identify areas needing improvement.
Compare your current cybersecurity practices with the new framework.
- Identify improvement areas and prioritize your efforts accordingly.
- Update cybersecurity policies and procedures.
Revise your policies and procedures based on gap analysis findings.
- Ensure updates are well-documented and communicated to all relevant stakeholders.
- Enhance supply chain risk management practices.
Assess your vendors’ and suppliers’ cybersecurity measures.
- Ensure they adhere to stringent security standards to minimize supply chain vulnerabilities.
- Invest in employee training and awareness programs.
Implement regular training programs to keep staff informed about the latest threats and best practices.
- Ensure employees understand their role in maintaining cybersecurity.
- Consider third-party assessments and audits.
Engage third-party experts to assess and audit your cybersecurity practices.
- Gain valuable insights and recommendations for improving your security posture and ensuring compliance with the new framework.
Partner With a Cybersecurity Expert
If you’re unsure about what the NIST Cybersecurity Framework 2.0 means for your business or need assistance with your IT and security needs, reach out to the experts at Deerwood Technologies. Our team is well-versed in the latest cybersecurity practices and can help you navigate the complexities of implementing the new framework.
At Deerwood Technologies, we offer comprehensive cybersecurity services tailored to your business’s unique needs. From conducting gap analyses to enhancing supply chain security and providing employee training, we have the expertise to ensure your business stays protected.
Contact Deerwood Technologies today to learn more about how we can help you strengthen your cybersecurity posture and safeguard your business against potential threats.